
by | Aug 10, 2017 | AMI in the News
NORCROSS, GEORGIA: – AMI, a global leader in BIOS and UEFI firmware, server and remote management tools, data storage products and unique solutions based on the Linux® and Android™ operating systems, is pleased to announce Aptio® V UEFI firmware support for the...

by | Aug 10, 2017 | Tech Blog
Today, AMD announced the launch of their AMD Ryzen™ Threadripper™ Processors. AMI Aptio®V UEFI firmware is the reference BIOS on the AMD Ryzen™ Threadripper™ Processors and AMD EPYC™ 7000 Series data center processors and platforms. Here are some of our...

by | Aug 7, 2017 | Tech Blog
Previously we covered the future of smarter homes through automation and IoT. But on a larger scale, another topic comes to mind: smart cities. With increasing levels of urbanization and influx of people moving to urban areas, the concept of smart cities has become...

by | Aug 3, 2017 | Tech Blog
BIOS RoT is not about a piece of rotting code. It’s about trust. RoT or Root of Trust is based on the idea that you trust something that is part of something else that is already trusted. An example of this would be an infant girl having absolute trust in her...

by | Jul 28, 2017 | AMI in the News
NORCROSS, GEORGIA: – AMI, a global leader in BIOS and UEFI firmware, server and remote management tools, data storage products and unique solutions based on the Linux® and Android™ operating systems, has added improved support for increased platform security...

by | Jul 27, 2017 | AMI in the News
NORCROSS, GEORGIA: – AMI, a global leader in BIOS and UEFI firmware, server and remote management tools, data storage products and unique solutions based on the Linux® and Android™ operating systems, has enabled NVMe® namespace management support for NVMe...

by | Jul 20, 2017 | Tech Blog
It is generally accepted that POST (or Power-On Self-Test) is basically what takes place right after you power-on a system or device. In the 1990s, as part of POST, the BIOS would test the memory. The more memory you had, the longer the test would take. Think a few...

by | Jul 17, 2017 | Tech Blog
If you keep up with AMI, other IBVs and technology companies, you may have heard the term “plugfest” popping up every so often. AMI happens to plan, host, sponsor and attend various plugfests throughout the year and you may be wondering, what is a...
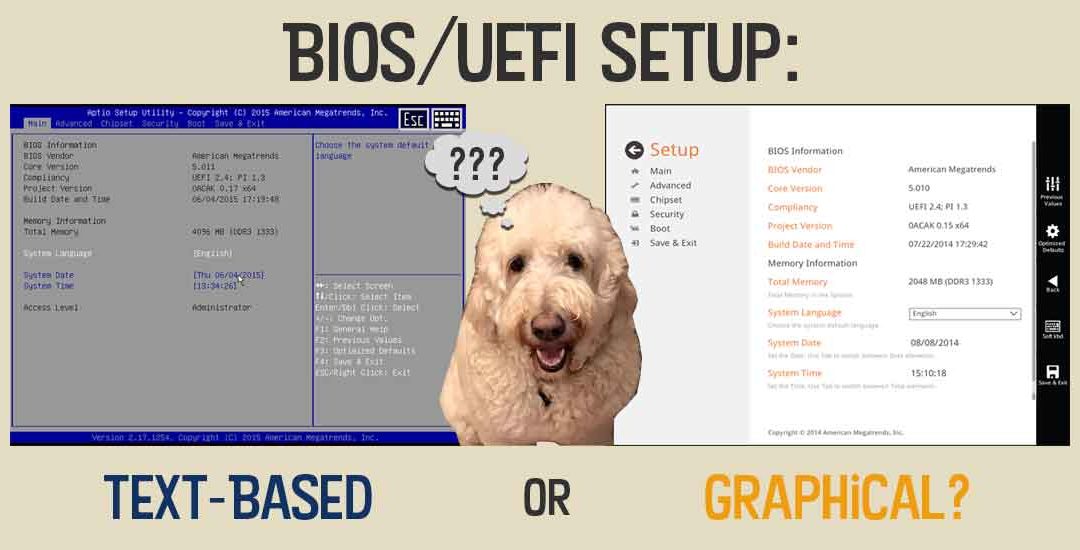
by | Jul 13, 2017 | Tech Blog
I was recently asked, “What is your biggest BIOS (UEFI) innovation?” From a techie point-of-view, I would have to say graphical setup in our client BIOS offering, AptioV… and not just any graphical setup, but Aptio ESA. (Extensible Setup...

by | Jul 3, 2017 | Tech Blog
Firmware is everywhere; in every system and nearly every technology device we use on a daily basis – clearest example would be computers/laptops. Firmware is also highly vulnerable to malware attacks, where hackers corrupt the firmware to create persistent...
















