AMI Security Advisories
Read the statement from AMI’s Chief Information Security Officer.
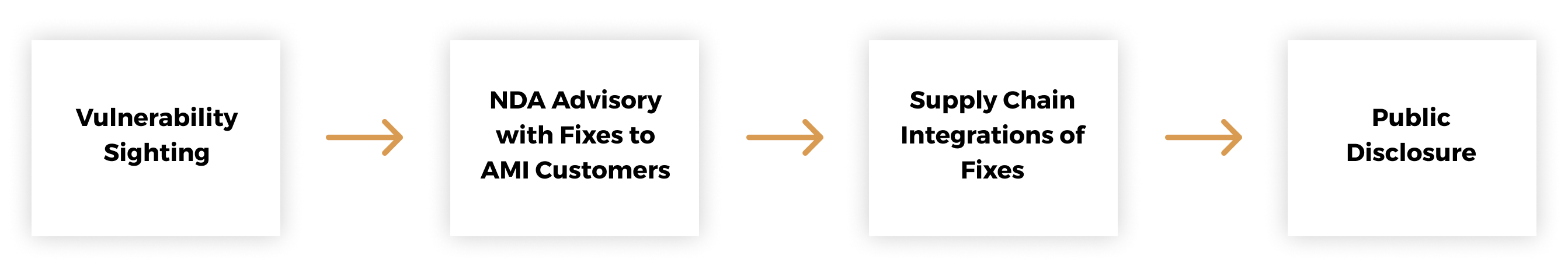
For customers who have questions related to security advisories, please contact AMI Sales Representative.
AMI Security Advisories:
Document and CVE #s to be provided when available
AMI-SA-2025005
| Vulnerabilities | CVSS Score | AMI Security Advisory | Published Date | Last Revised |
| CVE-2025-33043 | 5.8 | AMI-SA-2025005 | 05/29/25 | 05/29/25 |
AMI-SA-2025004
| Vulnerabilities | CVSS Score | AMI Security Advisory | Published Date | Last Revised |
| CVE-2024-42446 | 7.5 | AMI-SA-2025004 | 05/13/25 | 05/13/25 |
AMI-SA-2025003
| Vulnerabilities | CVSS Score | AMI Security Advisory | Published Date | Last Revised |
| CVE-2024-54084 | 7.5 | AMI-SA-2025003 | 03/11/25 | 03/13/25 |
| CVE-2024-54085 | 10.0 | AMI-SA-2025003 | 03/11/25 | 03/13/25 |
AMI-SA-2025002
| Vulnerabilities | CVSS Score | AMI Security Advisory | Published Date | Last Revised |
| CVE-2024-33659 |
5.7 | AMI-SA-2025002 | 02/11/25 | 02/11/25 |
AMI-SA-2025001
| Vulnerabilities | CVSS Score | AMI Security Advisory | Published Date | Last Revised |
| CVE-2024-42444 | 7.5 | AMI-SA-2025001 | 01/14/25 | 01/14/25 |
AMI-SA-2024004
| Vulnerabilities | CVSS Score | AMI Security Advisory | Published Date | Last Revised |
| CVE-2024-2315 | 6.8 | AMI-SA-2024004 | 11/12/24 | 11/12/24 |
| CVE-2024-33658 | 4.4 | AMI-SA-2024004 | 11/12/24 | 11/12/24 |
| CVE-2024-33660 | 5.2 | AMI-SA-2024004 | 11/12/24 | 11/12/24 |
| CVE-2024-42442 | 7.2 | AMI-SA-2024004 | 11/12/24 | 11/12/24 |
AMI-SA-2024003
| Vulnerabilities | CVSS Score | AMI Security Advisory | Published Date | Last Revised |
| CVE-2024-33657 | 7.8 | AMI-SA-2024003 | 8/19/24 | 8/19/24 |
| CVE-2024-33656 | 7.8 | AMI-SA-2024003 | 8/19/24 | 8/19/24 |
AMI-SA-2024002
| Vulnerabilities | CVSS Score | AMI Security Advisory | Published Date | Last Revised |
| CVE-2018-25103 | 2.3 | AMI-SA-2024002 | 4/15/24 | 7/09/24 |
AMI-SA-2024001
| Vulnerabilities | CVSS Score | AMI Security Advisory | Published Date | Last Revised |
| CVE-2023-45229 | 6.5 | AMI-SA-2024001 | 1/16/24 | 1/16/24 |
| CVE-2023-45230 | 8.3 | AMI-SA-2024001 | 1/16/24 | 1/16/24 |
| CVE-2023-45231 | 6.5 | AMI-SA-2024001 | 1/16/24 | 1/16/24 |
| CVE-2023-45232 | 7.5 | AMI-SA-2024001 | 1/16/24 | 1/16/24 |
| CVE-2023-45233 | 7.5 | AMI-SA-2024001 | 1/16/24 | 1/16/24 |
| CVE-2023-45234 | 8.3 | AMI-SA-2024001 | 1/16/24 | 1/16/24 |
| CVE-2023-45235 | 8.3 | AMI-SA-2024001 | 1/16/24 | 1/16/24 |
AMI-SA-2023010
| Vulnerabilities | CVSS Score | AMI Security Advisory | Published Date | Last Revised |
| CVE-2023-37293 | 9.6 | AMI-SA-2023010 | 1/09/24 | 1/09/24 |
| CVE-2023-37296 | 8.3 | AMI-SA-2023010 | 1/09/24 | 1/09/24 |
| CVE-2023-37297 | 8.3 | AMI-SA-2023010 | 1/09/24 | 1/09/24 |
| CVE-2023-37295 | 8.3 | AMI-SA-2023010 | 1/09/24 | 1/09/24 |
| CVE-2023-37294 | 8.3 | AMI-SA-2023010 | 1/09/24 | 1/09/24 |
| CVE-2023-3043 | 9.6 | AMI-SA-2023010 | 1/09/24 | 1/09/24 |
| CVE-2023-34333 | 7.8 | AMI-SA-2023010 | 1/09/24 | 1/09/24 |
| CVE-2023-34332 | 7.8 | AMI-SA-2023010 | 1/09/24 | 1/09/24 |
AMI-SA-2023009
| Vulnerabilities | CVSS Score | AMI Security Advisory | Published Date | Last Revised |
| CVE-2023-39538 | 7.5 | AMI-SA-2023009 | 12/06/23 | 12/06/23 |
| CVE-2023-39539 | 7.5 | AMI-SA-2023009 | 12/06/23 | 12/06/23 |
AMI-SA-2023008
| Vulnerabilities | CVSS Score | AMI Security Advisory | Published Date | Last Revised |
| CVE-2023-39535 | 7.5 | AMI-SA-2023008 | 11/14/23 | 11/14/23 |
| CVE-2023-39536 | 7.5 | AMI-SA-2023008 | 11/14/23 | 11/14/23 |
| CVE-2023-39537 | 7.5 | AMI-SA-2023008 | 11/14/23 | 11/14/23 |
AMI-SA-2023007
| Vulnerabilities | CVSS Score | AMI Security Advisory | Published Date | Last Revised |
| CVE-2023-34469 | 4.9 | AMI-SA-2023007 | 09/12/23 | 09/25/23 |
| CVE-2023-34470 | 6.8 | AMI-SA-2023007 | 09/12/23 | 09/25/23 |
AMI-SA-2023006
| Vulnerabilities | CVSS Score | AMI Security Advisory | Published Date | Last Revised |
| CVE-2023-34472 | 5.7 | AMI-SA-2023006 | 7/05/23 | 7/05/23 |
| CVE-2023-34473 | 6.6 | AMI-SA-2023006 | 7/05/23 | 7/05/23 |
| CVE-2023-34471 | 6.3 | AMI-SA-2023006 | 7/05/23 | 7/05/23 |
| CVE-2023-34337 | 7.6 | AMI-SA-2023006 | 7/05/23 | 7/05/23 |
| CVE-2023-34338 | 7.1 | AMI-SA-2023006 | 7/05/23 | 7/05/23 |
| CVE-2023-34329 | 9.1 | AMI-SA-2023006 | 7/18/23 | 7/18/23 |
| CVE-2023-34330 | 8.2 | AMI-SA-2023006 | 7/18/23 | 7/18/23 |
AMI-SA-2023005
| Vulnerabilities | CVSS Score | AMI Security Advisory | Published Date | Last Revised |
| CVE-2023-34344 | 5.3 | AMI-SA-2023005 | 6/12/23 | 6/12/23 |
| CVE-2023-25191 | 7.5 | AMI-SA-2023005 | 6/12/23 | 6/12/23 |
| CVE-2023-34345 | 6.5 | AMI-SA-2023005 | 6/12/23 | 6/12/23 |
| CVE-2023-34341 | 7.2 | AMI-SA-2023005 | 6/12/23 | 6/12/23 |
| CVE-2023-34342 | 6.0 | AMI-SA-2023005 | 6/12/23 | 6/12/23 |
| CVE-2023-34343 | 7.2 | AMI-SA-2023005 | 6/12/23 | 6/12/23 |
| CVE-2023-34334 | 7.2 | AMI-SA-2023005 | 6/12/23 | 6/12/23 |
| CVE-2023-34335 | 7.7 | AMI-SA-2023005 | 6/12/23 | 6/12/23 |
| CVE-2023-34336 | 8.1 | AMI-SA-2023005 | 6/12/23 | 6/12/23 |
AMI-SA-2023004
| Vulnerabilities | CVSS Score | AMI Security Advisory | Published Date | Last Revised |
| CVE-2023-29552 | 6.5 | AMI-SA-2023004 | 5/01/23 | 5/01/23 |
AMI-SA-2023003
| Vulnerabilities | CVSS Score | AMI Security Advisory | Published Date | Last Revised |
| CVE-2023-28863 | 5.9 | AMI-SA-2023003 | 4/04/23 | 4/04/23 |
AMI-SA-2023002
| Vulnerabilities | CVSS Score | AMI Security Advisory | Published Date | Last Revised |
| CVE-2023-25191 | 9.1 | AMI-SA-2023002 | 2/14/23 | 2/14/23 |
| CVE-2023-25192 | 5.3 | AMI-SA-2023002 | 2/14/23 | 2/14/23 |
AMI-SA-2023001
| Vulnerabilities | CVSS Score | AMI Security Advisory | Published Date | Last Revised |
| CVE-2022-40258 | 5.3 | AMI-SA-2023001 | 1/30/23 | 2/01/23 |
| CVE-2022-26872 | 8.3 | AMI-SA-2023001 | 1/30/23 | 2/01/23 |
| CVE-2022-40259 | 9.9 | AMI-SA-2023001 | 1/30/23 | 2/01/23 |
| CVE-2022-2827 | 7.5 | AMI-SA-2023001 | 1/30/23 | 2/01/23 |
| CVE-2022-40242 | 9.7 | AMI-SA-2023001 | 1/30/23 | 2/01/23 |
AMI-SA-2022001
| Vulnerabilities | CVSS Score | AMI Security Advisory | Published Date | Last Revised |
| CVE-2021-44769 | 4.9 | AMI-SA-2022001 | 12/20/22 | 12/20/22 |
| CVE-2021-46279 | 5.8 | AMI-SA-2022001 | 12/20/22 | 12/20/22 |
| CVE-2021-45925 | 5.3 | AMI-SA-2022001 | 12/20/22 | 12/20/22 |
| CVE-2021-4228 | 5.8 | AMI-SA-2022001 | 12/20/22 | 12/20/22 |
Report a Security Issue to AMI
Please provide as much information as possible, including:
- The products and versions affected.
- A detailed description of the vulnerability.
- Information on known exploits.
Aptio UEFI BIOS Firmware
MegaRAC BMC Firmware
Tektagon Firmware

Security ArticLes
Platform Root of Trust in Healthcare Can Be a Life-Saving Measure
The cybersecurity world has placed a good deal of attention on malware such as the Black Lotus bootkit, and the Android-based bank...
Five Best Coding Practices to Secure the Firmware Supply Chain
“Firmware presents a large and ever-expanding attack surface,” says the U.S. government in a joint report from the U.S. Department of Homeland...
Securing Arm®-based Servers with Platform Firmware Resiliency
In a February 2022 supply chain security report issued by the Department of Homeland Security, platform firmware was referred to as, “one of the...
Encryption Key for Secure Data Transmission
AMI recommends that you encrypt sensitive information to protect it from being viewed by unintended recipients. AMI can exchange emails with you using encryption. AMI highly suggests that you encrypt and decrypt email communications between AMI and yourself using an email client that supports encryption.
It is good security practice that you only trust validated encryption keys. Do not trust encryption keys that have not been validated. It is important to also validate your copy of the AMI public encryption key to ensure it is legitimate.
AMI Security Team Key Information
- User-ID: AMI Product Security Incident Response Team [email protected]
- Created: Apr 15 18:49:27 UTC 2025
- Expires: Apr 15 18:49:26 UTC 2027
- Type: 2048-bit RSA (secret key available)
- Usage: Signing, Encryption, Certifying User-IDs
- Fingerprint: 6e88bbdff4440f8e8eaf3750a4addcf1bf83c633
Please note that this encryption key is for both the MegaRAC and BIOS security. However, please use the AMI Security Team Key Information as provided above.
DOWNLOAD LICENSE AGREEMENT
NOTICE SPECIFIC TO SOFTWARE AVAILABLE ON THIS WEBSITE (ami.com) OR ANY OTHER AMI OWNED, OPERATED, LICENSED OR CONTROLLED SITE
Any software that is made available to download from this server (“Software”) is the copyrighted work of AMI and/or its suppliers. Use of the Software is governed by the terms of the end user license agreement, if any, which accompanies or is included with the Software (“License Agreement”). An end user will be unable to install any Software that is accompanied by or includes a License Agreement, unless he or she first agrees to the License Agreement terms.
The Software is made available for downloading solely for use by end users according to the License Agreement. Any reproduction or redistribution of the Software not in accordance with the License Agreement is expressly prohibited by law and may result in severe civil and criminal penalties. Violators will be prosecuted to the maximum extent possible.
WITHOUT LIMITING THE FOREGOING, COPYING OR REPRODUCTION OF THE SOFTWARE TO ANY OTHER SERVER OR LOCATION FOR FURTHER REPRODUCTION OR REDISTRIBUTION IS EXPRESSLY PROHIBITED, UNLESS SUCH REPRODUCTION OR REDISTRIBUTION IS EXPRESSLY PERMITTED BY THE LICENSE AGREEMENT ACCOMPANYING SUCH SOFTWARE.
THE SOFTWARE IS WARRANTED, IF AT ALL, ONLY ACCORDING TO THE TERMS OF THE LICENSE AGREEMENT. EXCEPT AS WARRANTED IN THE LICENSE AGREEMENT, AMI HEREBY DISCLAIMS ALL WARRANTIES AND CONDITIONS WITH REGARD TO THE SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES AND CONDITIONS OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, TITLE AND NON-INFRINGEMENT.
FOR YOUR CONVENIENCE, AMI MAY MAKE AVAILABLE ON THIS SERVICE OR IN ITS SOFTWARE PRODUCTS, TOOLS AND UTILITIES FOR USE AND/OR DOWNLOAD. AMI DOES NOT MAKE ANY ASSURANCES WITH REGARD TO THE ACCURACY OF THE RESULTS OR OUTPUT THAT DERIVES FROM SUCH USE OF ANY SUCH TOOLS AND UTILITIES. PLEASE RESPECT THE INTELLECTUAL PROPERTY RIGHTS OF OTHERS WHEN USING THE TOOLS AND UTILITIES MADE AVAILABLE ON THIS SERVICE OR IN AMI SOFTWARE PRODUCTS.
RESTRICTED RIGHTS LEGEND. Any Software which is downloaded from this Server (ami.com) any other AMI owned, operated, licensed or controlled site for or on behalf of the United States of America, its agencies and/or instrumentalities (“U.S. Government”), is provided with Restricted Rights. Use, duplication, or disclosure by the U.S. Government is subject to restrictions as set forth in subparagraph (c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013 or subparagraphs (c)(1) and (2) of the Commercial Computer Software – Restricted Rights at 48 CFR 52.227-19, as applicable. Manufacturer is AMI 3095 Satellite Boulevard, Building 800, Suite 425, Duluth, GA 30096.
NOTICE SPECIFIC TO DOCUMENTS AVAILABLE ON THIS WEBSITE
Permission to use Documents (such as white papers, press releases, datasheets and FAQs) from this server (ami.com) any other AMI owned, operated, licensed or controlled site (“Server”) is granted, provided that (1) the below copyright notice appears in all copies and that both the copyright notice and this permission notice appear, (2) use of such Documents from this Server is for informational and non-commercial or personal use only and will not be copied or posted on any network computer or broadcast in any media and (3) no modifications of any Documents are made. Educational institutions ( specifically K-12, universities and state community colleges) may download and reproduce the Documents for distribution in the classroom. Distribution outside the classroom requires express written permission. Use for any other purpose is expressly prohibited by law and may result in severe civil and criminal penalties. Violators will be prosecuted to the maximum extent possible.
Documents specified above do not include the design or layout of the ami.com website or any other AMI owned, operated, licensed or controlled site. Elements of AMI websites are protected by trade dress, trademark, unfair competition and other laws and may not be copied or imitated in whole or in part. No logo, graphic, sound or image from any AMI website may be copied or retransmitted unless expressly permitted by AMI.
AMI AND/OR ITS RESPECTIVE SUPPLIERS MAKE NO REPRESENTATIONS ABOUT THE SUITABILITY OF THE INFORMATION CONTAINED IN THE DOCUMENTS AND RELATED GRAPHICS PUBLISHED ON THIS SERVER FOR ANY PURPOSE. ALL SUCH DOCUMENTS AND RELATED GRAPHICS ARE PROVIDED “AS IS” WITHOUT WARRANTY OF ANY KIND. AMI AND/OR ITS RESPECTIVE SUPPLIERS HEREBY DISCLAIM ALL WARRANTIES AND CONDITIONS WITH REGARD TO THIS INFORMATION, INCLUDING ALL IMPLIED WARRANTIES AND CONDITIONS OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, TITLE AND NON-INFRINGEMENT. IN NO EVENT SHALL AMI AND/OR ITS RESPECTIVE SUPPLIERS BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF INFORMATION AVAILABLE FROM THIS SERVER.
THE DOCUMENTS AND RELATED GRAPHICS PUBLISHED ON THIS SERVER COULD INCLUDE TECHNICAL INACCURACIES OR TYPOGRAPHICAL ERRORS. CHANGES ARE PERIODICALLY ADDED TO THE INFORMATION HEREIN. AMI AND/OR ITS RESPECTIVE SUPPLIERS MAY MAKE IMPROVEMENTS AND/OR CHANGES IN THE PRODUCT(S) AND/OR THE PROGRAM(S) DESCRIBED HEREIN AT ANY TIME.
NOTICES AND PROCEDURE FOR MAKING CLAIMS OF COPYRIGHT INFRINGEMENT
Pursuant to Title 17, United States Code, Section 512(c)(2), notifications of claimed copyright infringement should be sent to Service Provider’s Designated Agent. ALL INQUIRIES NOT RELEVANT TO THE FOLLOWING PROCEDURE WILL NOT RECEIVE A RESPONSE.
See Notice and Procedure for Making Claims of Copyright Infringement.
LINKS TO THIRD PARTY SITES
THE LINKS IN THIS AREA WILL LET YOU LEAVE AMI’S SITE. THE LINKED SITES ARE NOT UNDER THE CONTROL OF AMI AND AMI IS NOT RESPONSIBLE FOR THE CONTENTS OF ANY LINKED SITE OR ANY LINK CONTAINED IN A LINKED SITE, OR ANY CHANGES OR UPDATES TO SUCH SITES. AMI IS NOT RESPONSIBLE FOR WEBCASTING OR ANY OTHER FORM OF TRANSMISSION RECEIVED FROM ANY LINKED SITE. AMI IS PROVIDING THESE LINKS TO YOU ONLY AS A CONVENIENCE, AND THE INCLUSION OF ANY LINK DOES NOT IMPLY ENDORSEMENT BY AMI OF THE SITE.
UNSOLICITED IDEA SUBMISSION POLICY
Neither AMI, nor its employees, agents and/or subsidiaries, shall accept or consider unsolicited ideas, including but not limited to ideas for new advertising campaigns, new promotions, new products or technologies, processes, materials, marketing plans or new product names. Submission of any original creative artwork, samples, demos, or other works to AMI is expressly prohibited. In the event a submission including unsolicited materials of any nature is received by AMI, said submission shall be destroyed and AMI shall not be liable for any direct or consequential damages suffered by the sender, nor shall AMI be under any obligation to treat such material as confidential or proprietary. It is expressly understood that the rationale for AMI’s policy on unsolicited idea submission is to prevent a third party from making a claim of infringement against AMI on the basis of an idea, product, or other material that is developed by AMI, that may be similar to or the same as an idea, product, or other material contained in an unsolicited submission that may have been submitted to and/or received by AMI.
FEEDBACK AND INFORMATION
ANY FEEDBACK YOU PROVIDE AT THIS SITE SHALL BE DEEMED TO BE NON-CONFIDENTIAL. AMI IS FREE TO USE SUCH INFORMATION ON AN UNRESTRICTED BASIS.





