A quick scan of recent news headlines, such as the attack on US company SolarWinds that reportedly affected hundreds of enterprises and government agencies, confirms that hackers continue to develop innovative ways to gain a persistent and undetectable way to control systems with valuable information and to siphon that information for nefarious purposes.
Due to its privileged level of execution and difficulty for operating systems and security software to detect unauthorized changes, system firmware is quickly becoming the newest and most prominent target for malicious actors – making it an area that demands increasing focus from security experts, system manufacturers and others. Intel TXT and TPM, coupled with complying BIOS provides firmware integrity assurance through remote attestation, giving confidence that the current firmware is not compromised.
Yet is that sufficient? What if a malicious hacker can access RAM content, exposing any data or workload running on that platform? Is there a more reliable solution that protects data in use?
Securing Cloud & Edge Workloads
Cloud adoption has accelerated, thanks in part to recent COVID-induced remote work and learning needs. One result of this growth is that workloads from competing businesses are often running on the same hardware that is hosted by a cloud vendor. The overarching question for administrators in these datacenters and cloud service providers is how to assure their customers that their workloads are protected from other tenants running on the same platform. What options are available to these customers to confidently move their compute workloads to the cloud?
For similar reasons, end users’ expectations on network bandwidth and latency have increased tremendously. To meet this demand, telco and datacenter operators continue to add edge infrastructure. Yet with increased remote infrastructure comes the concern of securing the workloads running on this remote hardware. How can a telco service provider be confident that their workloads are secure even if their remote infrastructure is compromised?
To address these security and trust challenges, the AMI TruE™ Trusted Environment Platform Security Solution leverages Intel® Software Guard Extensions (Intel® SGX) and Intel® Security Libraries for Data Centers to deliver a true trusted environment for confidential computing and secure cloud and edge workloads – read on to learn how!
Intel® Software Guard Extensions
Intel® Software Guard Extensions (Intel® SGX) delivers runtime protection of workloads using hardware-based memory encryption that isolates specific application code and data in memory. It allows user-level code to allocate private regions of memory, called SGX enclaves, that are designed to be protected from processes running at higher privilege levels.
Code and data in an SGX enclave are encrypted by a cryptographic key generated in the CPU package. They are decrypted only when they reach the confines of the CPU package. The code and data in an enclave cannot be leaked to any software on the platform – including privileged software like the OS kernel, the Virtual Machine Manager (VMM), the system BIOS or other system firmware. SGX attestation allows a remote party to verify that an SGX enclave is genuine. To support attestation at runtime, specific actions need to be taken by the enclave’s developer, the datacenter owner, and the remote party.
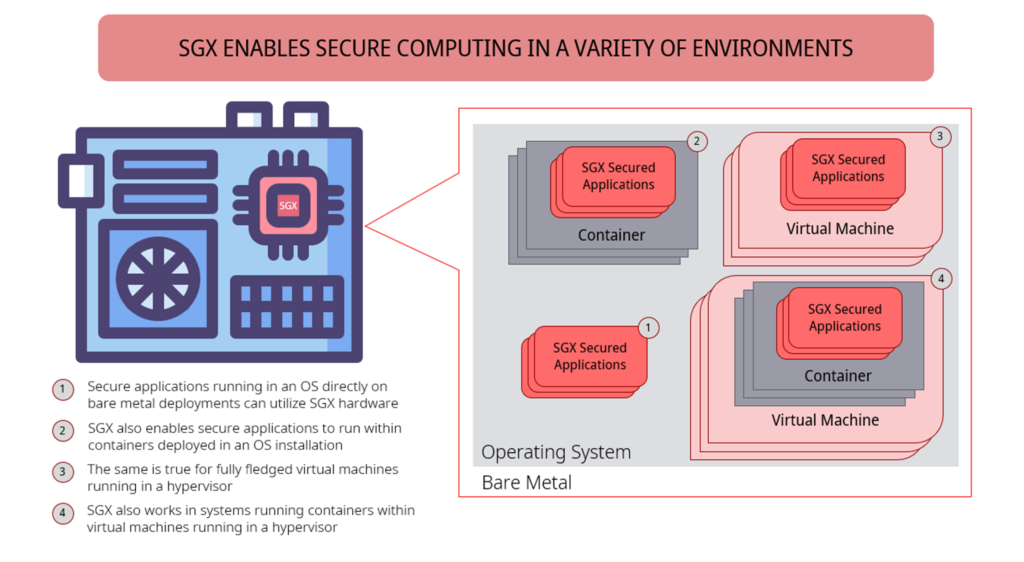
Cloud and telco vendors can use Intel SGX to confidently offload their sensitive data processing to remote untrusted edge infrastructure. Likewise, customers can also be assured that their workloads will be isolated and protected even with cloud and telco service providers. To learn more about how SGX works, visit https://www.intel.com/content/www/us/en/architecture-and-technology/software-guard-extensions.html.
AMI TruE: A Solution for Confidential Computing and Trusted Cloud Execution
Innovation in firmware security demands a deep understanding of firmware and its development. With over 35 years of BIOS, UEFI and BMC firmware development experience, AMI is perfectly positioned to enhance firmware security for the industry and deliver trust at the platform level. As a longstanding partner of Intel Corporation, AMI collaborates closely with Intel in the delivery of leading-edge firmware and security technologies such as Intel SGX.
AMI also strives for and takes pride in easing the adoption of Intel solutions and technologies by customers and end users. AMI TruE is great example of this winning collaboration – a holistic data center security solution from AMI that provides a Trusted Environment for cloud execution using Intel® Security Technologies and Intel® Security Libraries for Data Centers that is scalable, extensible and is built for cloud-to-edge applications. Leveraging Intel® SGX, AMI TruE enables confidential computing, eases deployment of workload attestation and secures application keys without compromising confidentiality. AMI TruE™ also establishes and tracks servers’ trusted compute status in the data center, enables compliance with data sovereignty regulations, runs sensitive workloads on trusted servers and provides remediation measures for untrusted platforms.
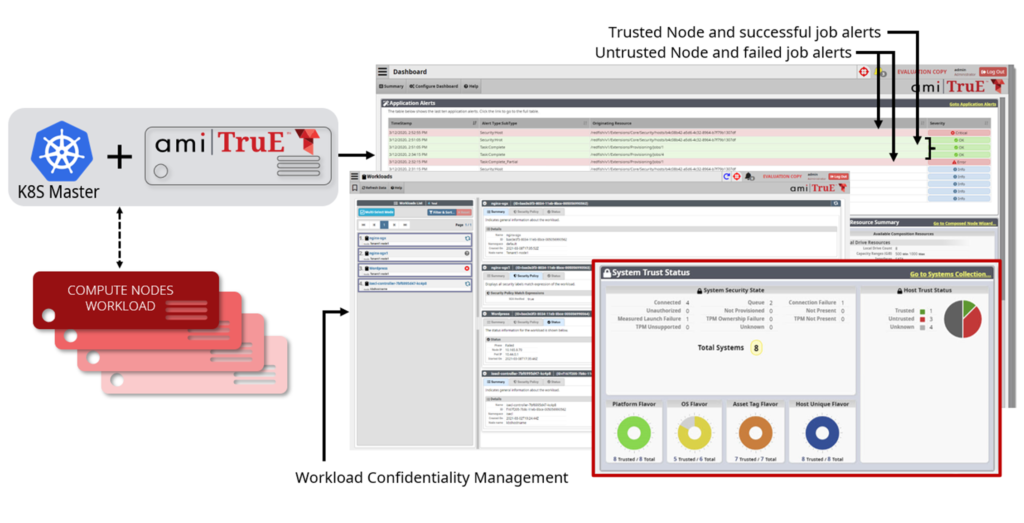
Deploying AMI TruE automatically installs required Intel® Sec-L components including SGX Quote Verification Service (SQVS), SGX Caching Service (SCS) and SGX Agent on hosts. Once deployed and configured, AMI TruE starts discovering servers and collects detailed asset information of all discovered servers.
Other key features and benefits of AMI TruE include:
- Dashboard displaying trust and workload confidentiality details of managed infrastructure
- Management of secure workloads on SGX enabled platforms
- Provisioning of PCK certificates for SGX enabled platforms and SGX collateral
- Labeling of nodes in a Kubernetes® cluster with trust status and SGX support
- Discovery of manageable platforms with security features including TPM and Intel SGX
- Remote provisioning of Trust Agents and SGX Agents
- Platform Integrity Assurance to ensure the system boots in a trusted state
- Data sovereignty to guarantee that geographic specific workloads only run where they are intended to
- Monitoring of the Trust status of all TPM enabled platforms
- Alerts when platform trust status is compromised.
- Telemetry and instrumentation for management and remediation: Remotely update BIOS or BMC firmware, install Operating System, rebooting the platform, etc.
- REST APIs for automation and integration
Finally, using Intel® Security Libraries for Datacenters (Intel® SecL-DC), AMI TruE supports Kubernetes® orchestration for launching workloads in secure enclaves.
For more information on the AMI TruE Platform Security Solution, visit ami.com/true, contact AMI via ami.com/contact or call 1-800-828-9264 to speak with an AMI Security Solutions Expert.
KUBERNETES® is a registered trademark of the Linux Foundation in the United States and other countries and is used pursuant to a license from the Linux Foundation. All other trademarks and registered trademarks are the property of their respective owners.



